BlueFlag Security Emerges from Stealth. Read Press Release

Advance SDLC security and governance with BlueFlag Security Identity Intelligence framework
SECURE YOUR IDENTITIES
Empower your organization to effectively remove excessive permissions, strengthen identity hygiene, and reduce risky behavior with the BlueFlag Security platform, designed for human and machine developer identities.
Utilize BlueFlag’s AI/ML Identity Intelligence framework to actively mitigate identity risks and avoid compliance drift.
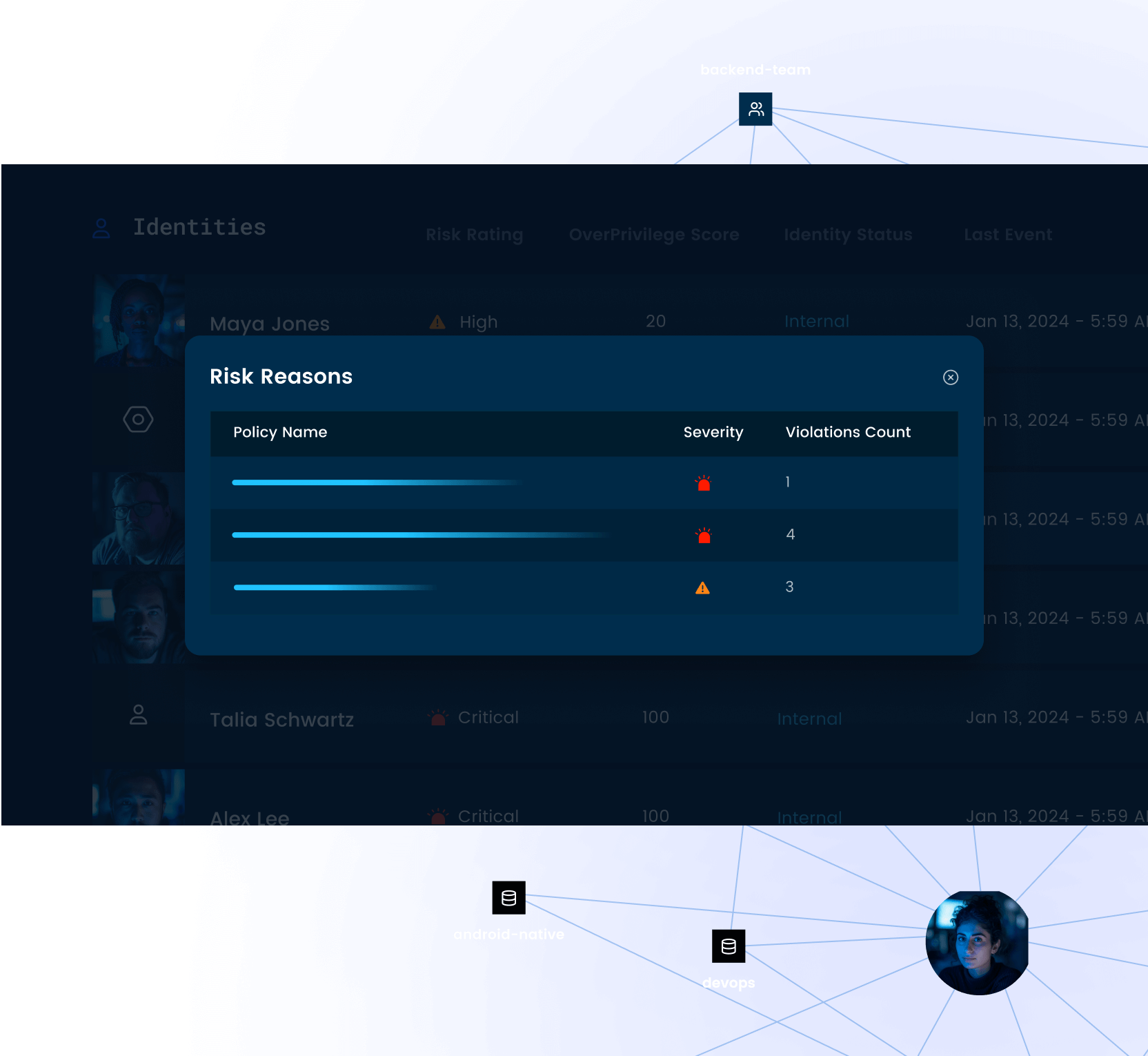
Gain critical identity insights, ranked by priority, safeguarding against unauthorized access, insider threats, and misconfigurations.
Turn alert fatigue into actionable intelligence quickly addressing identity threats for effective remediation.
Uncover hidden risks by analyzing identity activity patterns, behavior and anomalies.
SECURE YOUR TOOLS
Proactively validate the posture of developer tools with continuous monitoring, pinpointing misconfigurations and aligning with CI/CD best practices.
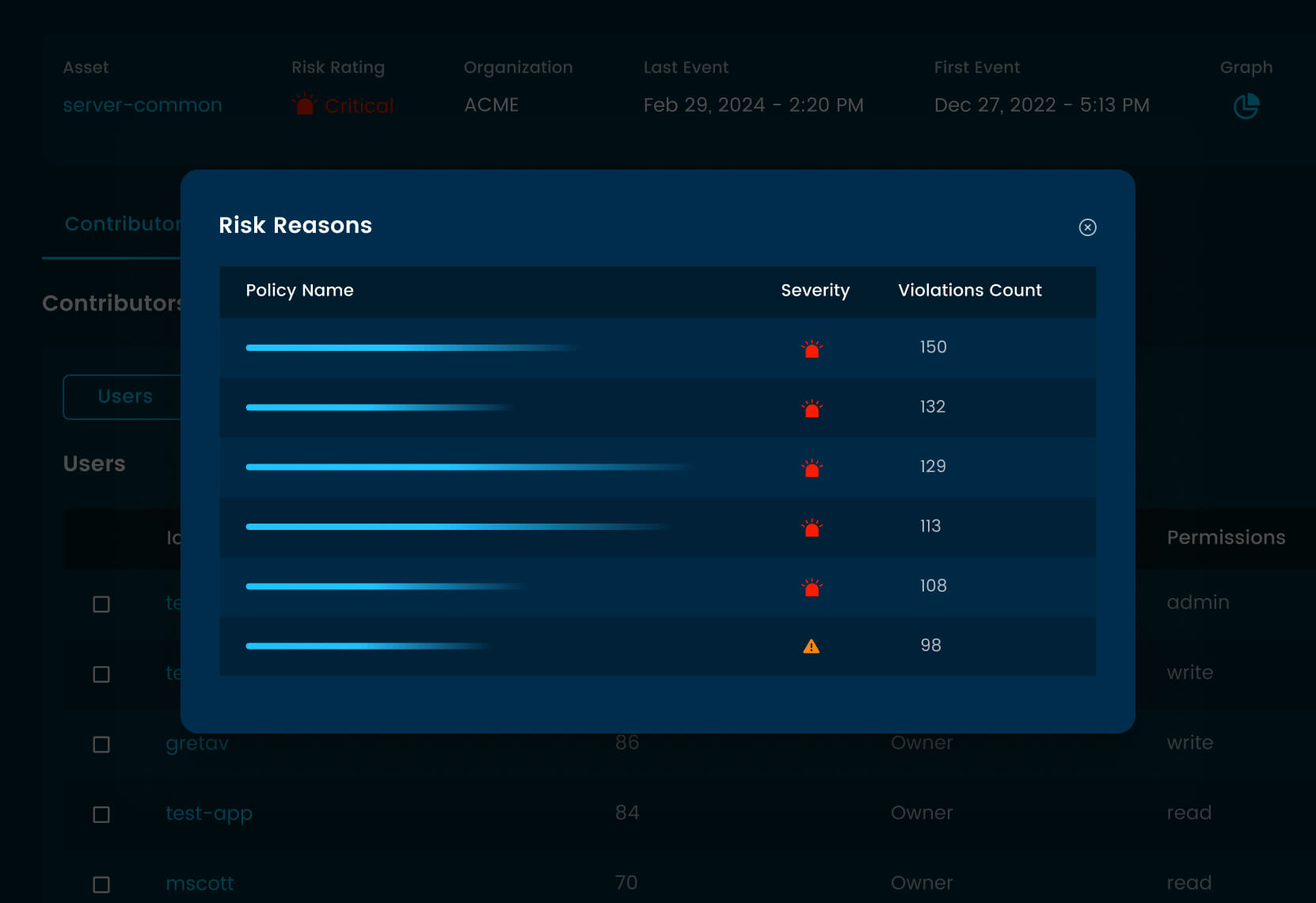
Uncover misconfigurations across the developer toolchain including source code management tools, CI/CD pipelines and container registries.
Highlight and contextualize critical security issues to cut through false positives for your team.
Streamline remediation with customizable policy templates that enforce best practices across your organization.
Uniformly apply consistent security best practices and policies to minimize the risk of human error.
SECURE YOUR CODE
Continuously scan application code to identify and prioritize critical open source vulnerabilities for streamlined remediation.
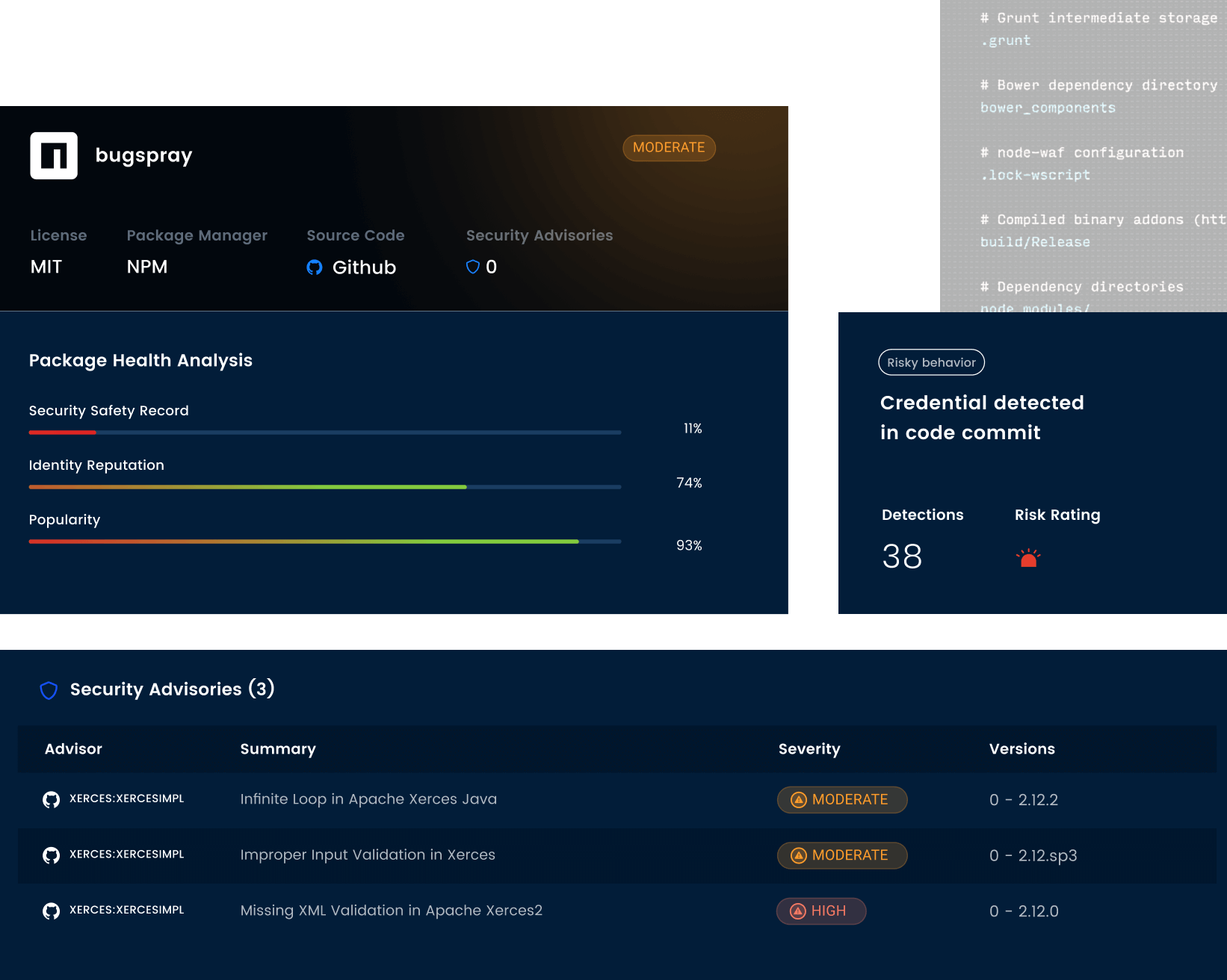
Identify and alert on new open-source software risks and vulnerabilities, with easy to sue customizable policies.
Generate and maintain up-to-date SBOMs in industry-standard formats mapped to code dependencies and build containers.
Continuously scan and remediate hardcoded secrets using workflows integrated with issue tracking software, and CI/CD pipelines.
Predict open-source software security risks by evaluating contributor reputations and historical safety records of packages.
Continuous SDLC compliance by design
Embeds industry standards into development environments through secure-by-design processes without overburdening teams.

Simplify adherence to ISO 27001, NIST 800-218, SOC2 and more by mapping and optimizing CI/CD processes to critical compliance controls.
Easily assess current and historical data to demonstrate adherence to regulatory policies and internal standards.
Instantly create customized compliance reports for auditors with just a click, from detailed analyses to executive summaries.
Ensure comprehensive compliance across identities, developer tools, and open-source software to manage all CI/CD risks.